What is encryption?
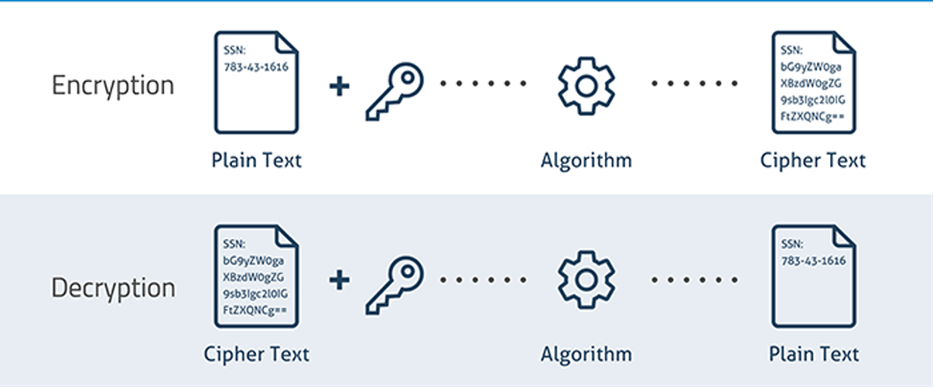
Encryption is a method of encoding data (messages or files) so that only authorized parties can read or access that data. It involves complex mathematical algorithms and digital keys to encode data into ciphertext.
Encryption can be as simple as changing characters by a set value. As encryption has evolved, cryptographers have added more layers and the process of decryption has become more complex. Historically used by the military and government in radio communications, today encryption is used to protect data stored on computers and storage devices, as well as data transmitted over networks.
To decrypt the message, both the sender and the recipient must use a “secret” encryption key which is a collection of algorithms that scramble and unscramble data back to a readable format.
Encryption of data primarily utilises one of two methods – Symmetric encryption or Asymmetric encryption. Understanding the differences between key encryption types and their uses in the modern day can be tricky. Let’s explore the primary categories.
Symmetric Encryption
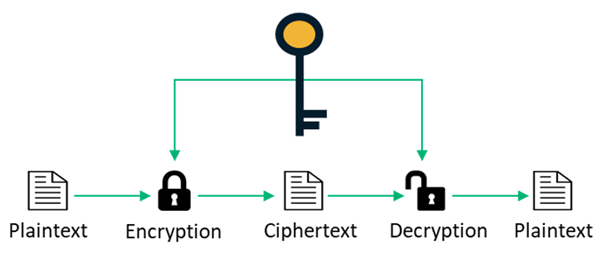
Symmetric encryption utilises the same key to encrypt and decrypt a piece of data. The secret key needs to be sent through a secure channel and the sender must make sure that the same key is used on the receiver end to decrypt the data. Additionally, Symmetric encryption suffers from issues with key leakage, where an organisation risks potential reconstruction of a secret key by an attacker while the key is still in use. Without proper key hierarchy support or effective key rotation, any application usage can leak information that attackers can use to reconstruct the secret key. By properly rotating keys, you can minimise both the chances of a key being reconstructed by an attacker, as well as minimising the amount of data that could be decrypted assuming the key is reconstructed.
Asymmetric Encryption
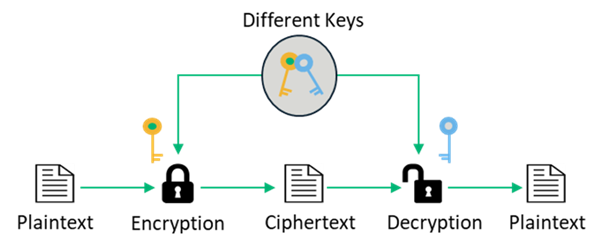
Asymmetric encryption method is the most common form of encryption used today. It utilises two different but mathematically related keys – the public key and private key. The public key is used for encryption, while the private key is used for decryption. As the name suggests, the private key must be private so that only an authorized recipient can decrypt the message. Simply put, the purpose of asymmetric key cryptography is to serve as a way to securely encrypt data in public channels while providing authentication and data integrity. Since it does not require key exchange, there are no key distribution issues that you would otherwise have with symmetric encryption. The most common everyday usage of asymmetric encryption is through HTTPS. A web server has a certificate (public key), and a user generates a private key that corresponds to the provided public key.
Web Security

Businesses should ensure that staff only access websites using TLS and that sites that are not secured with TLS are blocked by a web proxy. In the absence of a web proxy, use caution when accessing sensitive data in a web browser. Always ensure that the site is accessed using HTTPS and that the site certificate is valid.
HTTPS means that your connection to the site is secured with Transport Layer Security (TLS), formerly known as Secure Sockets Layer (SSL). Data is encrypted in transit and decrypted on both sides with verified digital certificates, which act as keys, as described above.
Why is encryption important?
Protects Your Intellectual Property, Business and Identity

A common attack used in lieu of ransomware is simply to steal all of an organisation’s unencrypted data and threaten to either make the data leak public or sell it to the highest bidder. Commonly the attacker will demand a ransom in exchange for keeping the leak private. Data lost in these attacks can be used to facilitate further attacks (in the case of compromised credentials), steal identities (if confidential personal information is lost) or benefit foreign actors or organisations (in the case of intellectual property being stolen).
File encryption is an important part of protecting against cyber-attacks, including ransomware. Once your data is encrypted, criminals cannot access your data without the decryption key. Instead, they only see the encrypted ciphertext, and will need to further compromise your systems in order to acquire sensitive data.
Protects your Lost/Stolen devices
As the usage of BYOD devices increases, so too does the risk to your organisation’s cybersecurity. A lost smartphone or laptop can be catastrophic for a business depending on the data stored on the device. Malicious actors can scan the internal drive and steal sensitive company data from the device. In the new age of hybrid work environments, an organisations data is now found in many home residences as well, all with differing levels of physical and logical security. The threat surface for an attack has never been larger.
File encryption protects against the threat of lost or stolen mobile devices. All storage mediums on employee devices should be encrypted at the root level and secured with a complex decryption key that is kept secret. This way, if a device is stolen, it is not possible to simply remove the internal storage device and steal data manually; the drive must be decrypted first.
References:
- Marget, A., 2020. Data Encryption: How It Works & Methods Used. [online] Unitrends. Available at: https://www.unitrends.com/blog/data-encryption#:~:text=Encryption%20uses%20complex%20mathematical%20algorithms,back%20into%20the%20original%20value.
- Rafte, D., 2022. What is encryption and how does it protect your data?. [online] Us.norton.com. Available at: <https://us.norton.com/internetsecurity-privacy-what-is-encryption.html#>
- Kath, H., 2021. How Encryption Works: Everything You Need to Know. [online] www.goanywhere.com. Available at: <https://www.goanywhere.com/blog/how-encryption-works-everything-you-need-to-know>
- Arampatzis, A., 2020. Encryption and Decryption – What’s the Difference? | Venafi. [online] Venafi.com. Available at: <https://www.venafi.com/blog/what-difference-between-encryption-and-decryption>
- DeWitt, D., 2021. Data Encryption: What Is It?. [online] Data Encryption: What Is It?. Available at: <https://www.avast.com/c-encryption
- Mukherjee, L., 2020. Symmetric vs Asymmetric Encryption – 5 Differences Explained by Experts. [online] InfoSec Insights. Available at: https://sectigostore.com/blog/5-differences-between-symmetric-vs-asymmetric-encryption/
- Now, H., 2022. Hacking concept. Personal information and credit card detail.. [online] iStock. Available at: <https://www.istockphoto.com/vector/hacking-concept-personal-information-and-credit-card-detail-gm1386270253-444621991>