Data breaches from ransomware or other viruses are becoming more common in today’s world. Protecting your business from a potential data loss has been elevated to the same level of importance as protecting your business from physical losses like fire and theft.
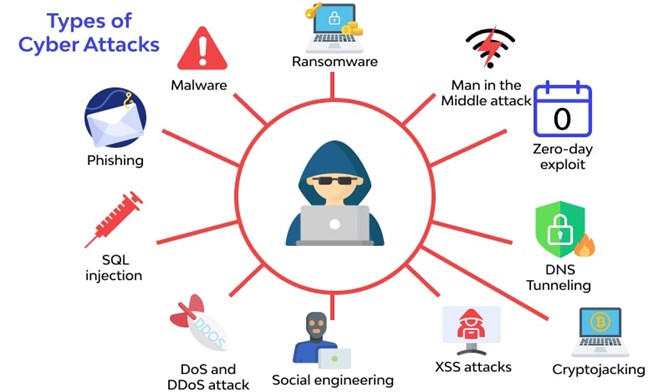
In the year 2021, cybercriminals unleashed a wave of cyber attacks that were not only highly coordinated, but also significantly more sophisticated than anything that had ever been seen before. Simple attacks on a single endpoint evolved into complex, multi-stage operations. Ransomware attacks are affecting SMBs and large corporations alike. Cybercriminals were even able to gain a foothold in company networks through cryptomining attacks. It was a year marked by massive data leaks, sophisticated phishing attacks, expensive ransomware payouts, and the emergence of a vast, new, and complex threat landscape.
When it comes to protecting an organisation from cyberattacks, the firewall is the first line of defence deployed at a network’s perimeter. Providing secure remote access, supporting high-performance computing, safeguarding cloud environments, and securing specialised systems are just some of the other areas where companies may have specific security requirements.
Here are the few key areas an organization needs to consider to avoid critical cyber attacks.
Plan your Firewall Deployment:
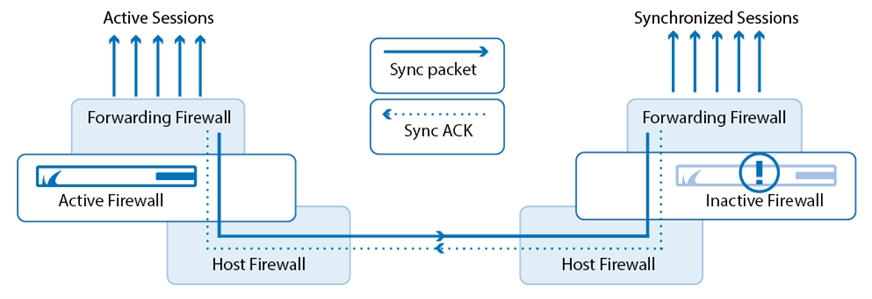
In a macro-segmented network, they monitor and control inbound and outbound access across network boundaries. This is true for both layer 3 routed firewall and layer 2 bridge firewall deployments. When deploying a firewall, these networks or zones are connected to the firewall’s network interfaces. The firewall policy can then be simplified using these zones. A perimeter firewall, for instance, will include an exterior zone connected to the Internet, one or more internal interfaces connected to internal networks, and maybe a DMZ network connection. The firewall policy can then be modified as required to provide granular control.
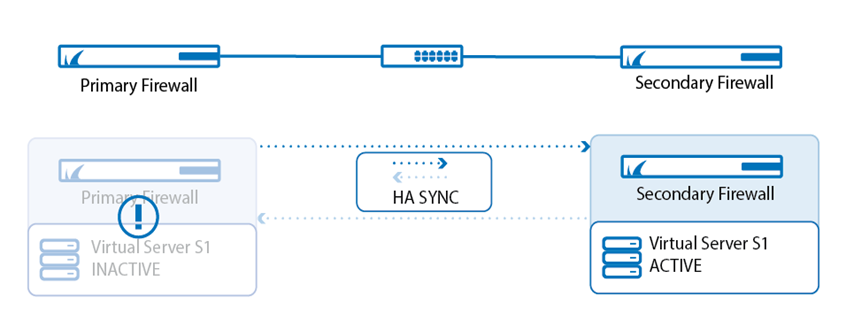
Additionally, deploying two or more in a High Availability (HA) cluster guarantees continued security in the event that one fails. A hyperscale network security solution is preferable because it continually utilises the resources of each cluster member. This should also be considered for networks that encounter seasonal traffic peaks.
Zero-trust implementation:
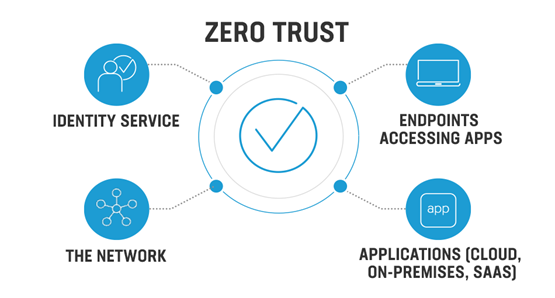
This network security philosophy says that no one inside or outside the network should be trusted unless their identity has been carefully checked. Zero-trust is based on the idea that threats can come from both inside and outside the network. These assumptions shape the way network administrators think, so they have to come up with strict security measures.
Multiple Factor Authentication (MFA), a security measure that calls for users to provide multiple credentials in order to gain access, is used in this verification. Zero-trust also includes Network Access Control (NAC), which is used to prevent unauthorised users and devices from gaining access to a corporate or private network. All network access is restricted to authenticated users and devices that comply with the network’s security policies.
Web application security:
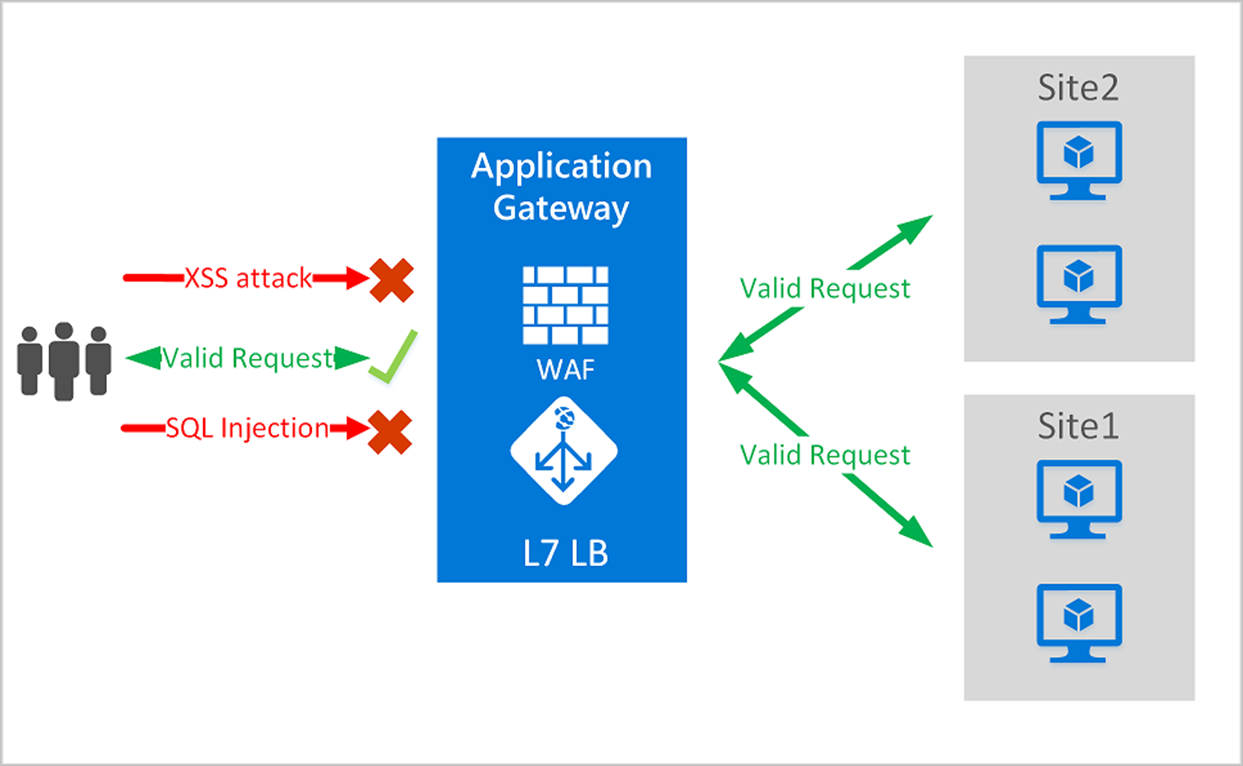
Expanding an organization’s attack surface is a common side effect of new digital endeavours. Vulnerabilities in web servers, server plugins or other flaws might expose new APIs and web applications to potentially malicious traffic. The latest features available in next generation firewalls help to protect web apps by filtering and monitoring HTTP/S traffic to and from a web service.
Email Gateway Security and Sandboxing:
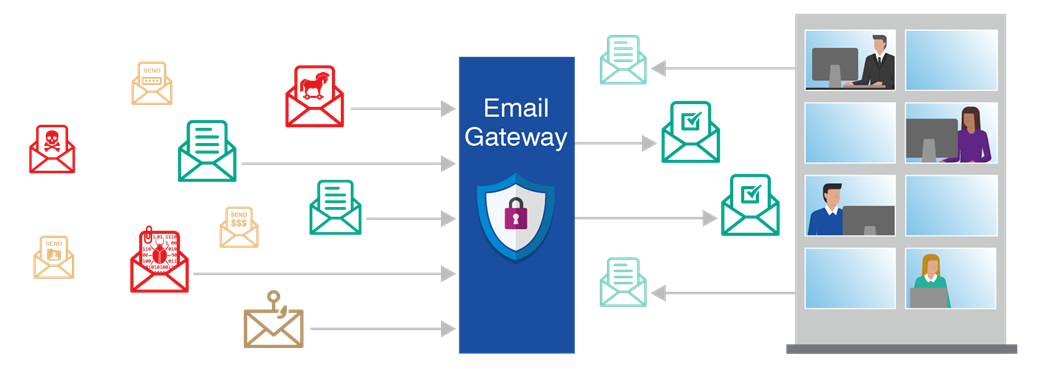
Email is a common attack vector for cybercriminals. In addition to sandboxing, a secure email gateway solution protects against email-based attacks with advanced multilayered defences. Before an email reaches your network or mail server, it can be examined to see whether it contains any unfamiliar links, senders, or file types that slipped through the email filter.
Threat intelligence sharing:
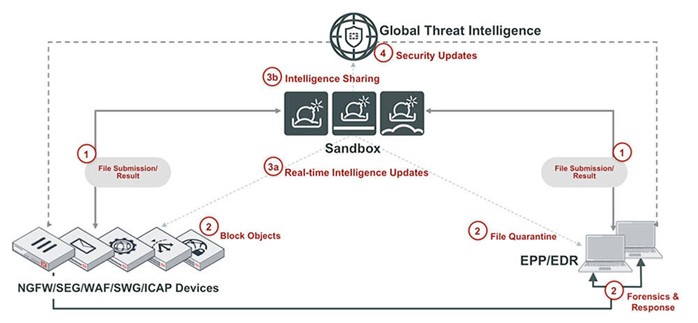
To help organisations mitigate hidden threats, real-time actionable intelligence is essential. For any network environment to offer a proactive defence, information must be shared among the various security layers and products. Additionally, this information sharing should include entities outside of your organisation that are part of the larger cybersecurity community, such as Computer Emergency Response Teams (CERTs), Information Sharing and Analysis Centres (ISACs), and business alliances like the Cyber Threat Alliance (CTA). The fastest way to respond to attacks is through rapid sharing, which also breaks the cyber kill chain before it mutates or spreads to other systems or organisations.
User Training and Good Cyber Hygiene:
The 2021 Verizon Data Breach Investigations report says that 85 percent of data breaches are caused due to human error. It is impossible to ever be completely secure, but training your employees in cyber awareness and basic security practices will dramatically reduce your organisation’s threat surface. Ensure that all employees are trained in how to spot phishing attempts and have easy methods to report suspicious cyber activity. Ensure they are trained in maintaining a high standard of cyber hygiene, and know how to keep their personal devices and home networks safe. Employees should go through training when they are hired and at regular intervals while they are working, so that the information stays up-to-date and fresh in their minds. Training should also be kept up-to-date and include any new security protocols that may need to be put in place.
Furthermore, implementing basic security tools and protocols can assist CISOs in establishing a baseline of defence at the most vulnerable edge of their network and ensuring the security of critical digital resources.
Implementing secure systems that adhere to strict protocols and government regulations can be hard. Cyberattacks are inevitable, and protecting your organisation from the daily flood of attacks can be a daunting task. If you need assistance preparing your business for the new age of security, don’t hesitate to contact us.
References:
- Check Point Software. 2022. 8 Firewall Best Practices for Securing the Network – Check Point Software. [online] Available at: <https://www.checkpoint.com/cyber-hub/network-security/what-is-firewall/8-firewall-best-practices-for-securing-the-network/> [Accessed 1 January 2022].
- Tarun, R., 2021. How to Prevent Ransomware: 9 Ways to Limit the Impact | Fortinet Blog. [online] Fortinet Blog. Available at: <https://www.fortinet.com/blog/industry-trends/how-to-prevent-ransomware-attacks-top-nine-things-to-keep-in-mind> [Accessed 6 December 2021].
- Parizo, E., 2019. The role of next-gen firewalls in an evolving security architecture. [online] InsiderPro. Available at: <https://www.idginsiderpro.com/article/3409084/the-role-of-next-gen-firewalls-in-an-evolving-security-architecture.html> [Accessed 27 July 2022].
- Barracuda Networks, I., 2022. High Availability. [online] Barracuda Campus. Available at: <https://campus.barracuda.com/product/cloudgenfirewall/doc/72516118/high-availability/> [Accessed 27 July 2022].
- 2022. Advanced Threat Protection and Intelligence | Fortinet. [online] Available at: <https://www.fortinet.com/solutions/enterprise-midsize-business/protect-advanced-threats> [Accessed 27 July 2022].
- Mitra, A., 2020. What is an Email Gateway and how does it work?. [online] The Security Buddy. Available at: <https://www.thesecuritybuddy.com/anti-spam/what-is-an-email-gateway-and-how-does-it-work/> [Accessed 27 July 2022].
- europa.eu. 2021. Cybersecurity: main and emerging threats in 2021 (infographic) | News | European Parliament. [online] Available at: <https://www.europarl.europa.eu/news/en/headlines/society/20220120STO21428/cybersecurity-main-and-emerging-threats-in-2021-infographic#missinglink> [Accessed 27 July 2022].